Welcome to Red S.W.O.R.D (Security Widespread Operations and Redteaming Division).
We offer our services in the field of cybersecurity, along with some solutions that you can test for free, and other useful resources.
Thank you for visiting and enjoy your browsing.
Site under construction ...
 redsword.io is online - [ 01/04/2024 ]
redsword.io is online - [ 01/04/2024 ]
I am very happy to have finally published the alpha version of the site. There is still a lot of work but we are closer to the end than the beginning.
This site will terminated for the publication of PANDORA INFINITY.
 Read more
Read more
 The USB Key Master - [ 01/04/2024 ]
The USB Key Master - [ 01/04/2024 ]
Today, many of us have many USB keys. If you are in IT world, maybe you own some higher than the majority. If you are in cyber security world, the number can be insane.
This article invites you to create a USB key ring dedicated to cyber security, based on the one you already have or on the models presented in the article, hoping that this can inspire you...
 Read more
Read more
PANDORA INFINITY can be qualified as an O.S.A.C.M.S (Offensive Security Activity and Content Management System) application and can be useful to all security professionals and enthusiasts.
The small size of the Raspberry PI will permit to have a flexibility solution and test many more other attack scenarios while Kali Linux provides best-in-class tools. So, connected to the User Interface, you will be able to audit many attack surfaces, find every weakness of each corner of your SI, perform differents type of pentests and much more.
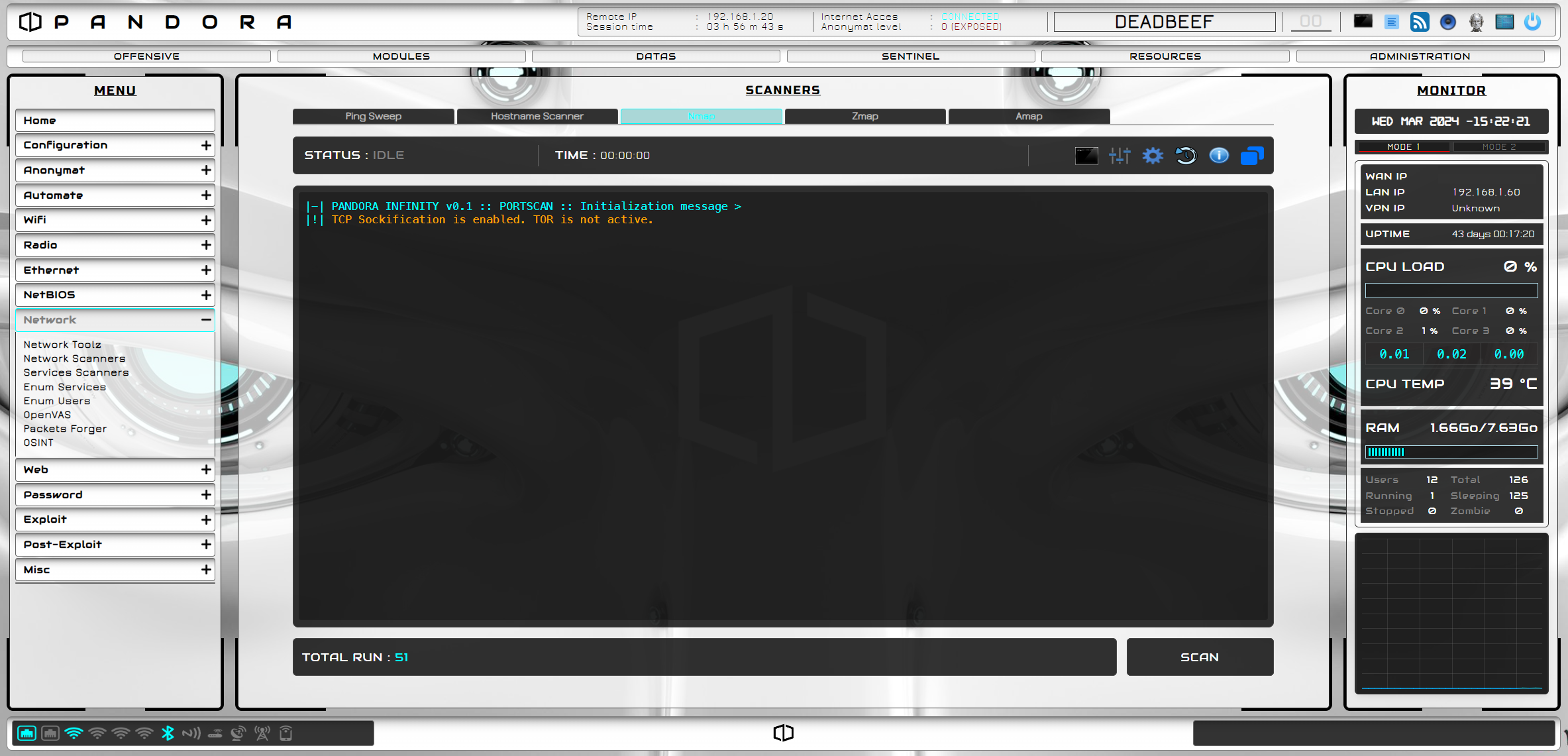
 Read more
Read more

PANDORA ZERO is dedicated to the audit/discovery of your digital environment and designed to be controlled from a smartphone/tablet in landscape mode with two thumbs.
The very small size of the Raspberry Pi0 2 and the powerful tools provided by Kali Linux will allow you to perform numerous security checks and carry out certain attack scenarios where it will be more difficult/less stealthy with others bulkier hardware.
Based on your need, you will be able to add some USB devices to expand the capabilities of the Raspberry Pi0 2 and be controlled with PANDORA ZERO.
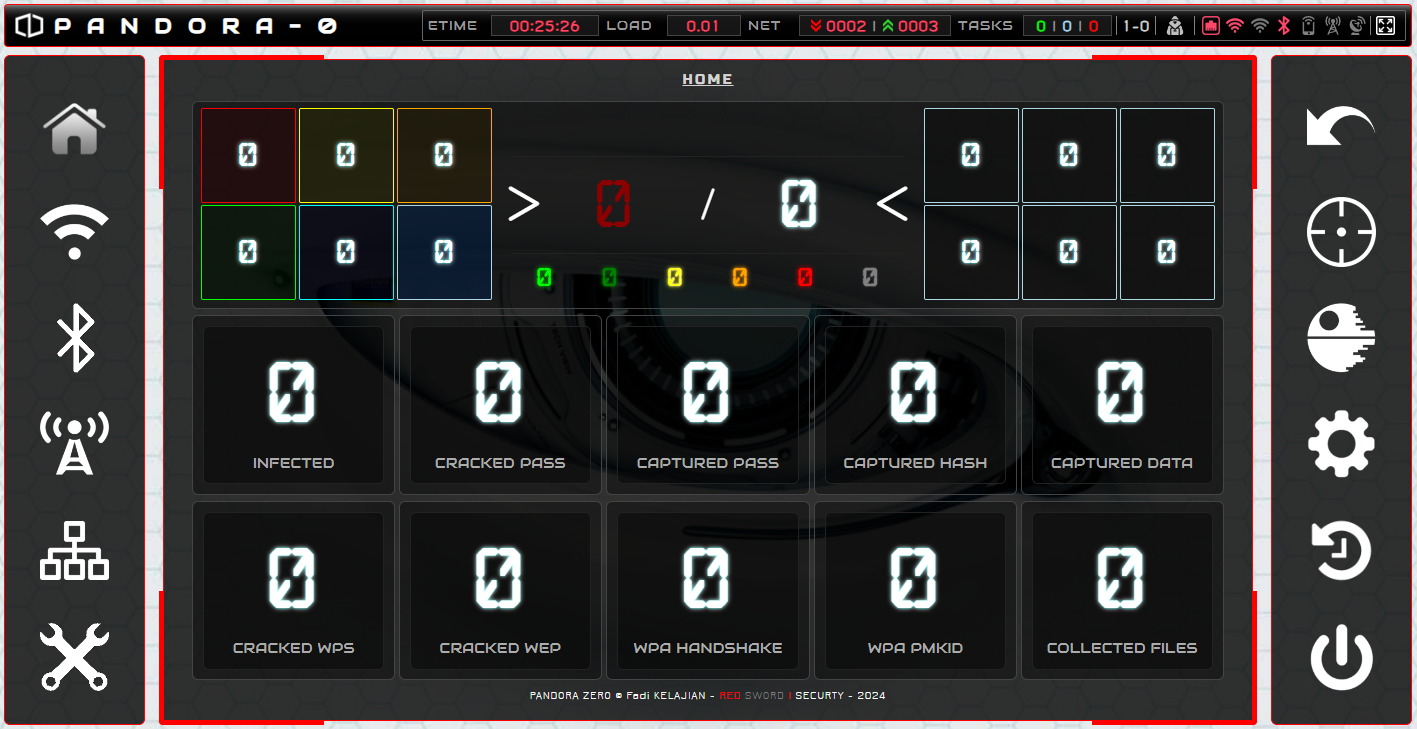
 Read more
Read more
 Wifi USB adapter for Kali Linux - [ 01/04/2024 ]
Wifi USB adapter for Kali Linux - [ 01/04/2024 ]
To improve your knowledge of WiFi security, and to be able to use the majority of wifi security tools, you will need a suitable WiFi card compatible with monitor mode,
injection capacity and off course, full supported in Kali Linux. In this article, you will find informations about some compatible card involved in our PANDORA projects and have been tested.
Hope, theses informations may be help you to acquire the right one for your need or will conforte you in your choice...
 Read more
Read more
 The USB Key Master - [ 01/04/2024 ]
The USB Key Master - [ 01/04/2024 ]
Today, many of us have many USB keys. If you are in IT world, maybe you own some higher than the majority. If you are in cyber security world, the number can be insane.
This article invites you to create a USB key ring dedicated to cyber security, based on the one you already have or on the models presented in the article, hoping that this can inspire you...
 Read more
Read more